The biggest data breaches in modern US history
Cyber attacks are unpleasant at least – and, unfortunately, every company is at high risk, no matter their size.
When targeting their victims, cyber criminals can modify, plunder, demolish or expose sensitive information. The objective is usually to access customer details, intellectual property, corporate and financial information, and other data types by implementing a range of common cyber threats.
In this short overview, we will dive into the 10 most harmful data breaches in modern US history and discuss the impact on the large organizations who have fallen victim to them.
Today’s insights
As to a 2021 ITRC report, the number of overall data compromises has grown over 68% if compared to 2020.
The number of victims continuously decreases, as criminals are shifting their attention to targeted data types. Yet still, the number of consumers that experience repeated compromise remains consistent, raising concerns.
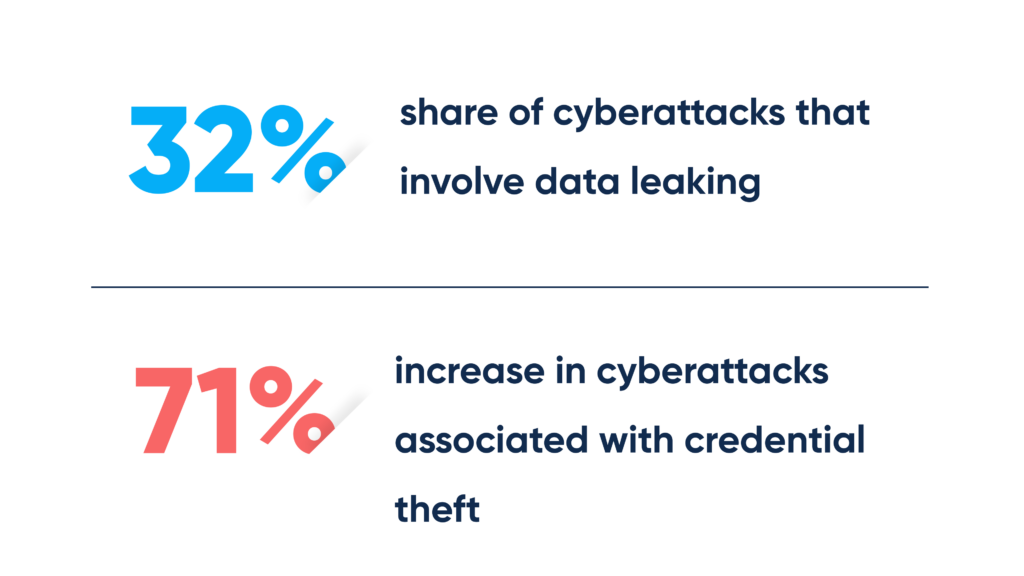
As to the 2024 IBM index, we contemplate:
- A trimming 71% increase in cyberattacks associated with credential theft
- A concerning 32% share of cyberattacks that involve data leaking
In 2023, the attackers have shifted towards logging into networks rather than using common hacking methods. What’s more, the perpetrators have transitioned from ransomware to malware mainly intended for theft, which indicates data leakage to have the most prevalent impact on organizations.
The 10 most remarkable security breaches in the last decade
Microsoft
Date: January 2021
Target: 30,000 companies in the United States, 60,000 worldwide
In one of the largest cyberattacks on record in the United States, 30,000 enterprises were impacted by an extensive breach that targeted Microsoft Exchange email servers that’s among world’s chief email platforms. The perpetrators have managed to leverage four separate zero-day vulnerabilities, thereby achieving unauthorized access to accounts from enterprises to local municipal entities.
For almost three months, the attackers have exploited programming faults to control susceptible systems.
Once inside, they obtained data access, deployed malware, established backdoors, and dominated the servers. Since those intrusion attempts have appeared to originate from the email servers, many end-users assumed these were legitimate and granted their permission.
Although identified security issues were fixed, many administrators must have manually updated their systems. If these weren’t applied, the discovered security vulnerabilities could have been easily exploited again.
Date: April 2021
Target: 530 million exposed users
The massive data breach has leaked personal information of over 530 million compromised users, which left their names, phone numbers, account details, and even their credentials brutally exposed to the public eye. The conundrum was detected within their contact syncing, adducing perpetrators that exploited a vulnerability for extracting customer information from profiles.
While Facebook wasn’t culpable for this data breach, it spotlighted concerns regarding third-party access. Following several data breaches, the company has eventually increased restrictions on their third-party vendors having access to their internal databases.
Date: April 2021
Target: 700+ million exposed users
In 2021, the identities of over 750 million individual users (about 93% of the entire database) were disclosed. Although most personal information was already publicly accessible, the exploit has violated the platform’s security terms and conditions.
The data scraped included:
- Full names
- Phone numbers
- Emails
- Usernames
- Geolocation records
- Linked accounts
Any exposed email addresses after such data breaches can be potentially subject to phishing and ransomware. While that personal information was mostly publicly accessible, it raised serious concerns regarding future potential exploitation of such to compile open-source intelligence (OSINT) databases.
What’s more, that presents an opportunity for attackers to compromise prominent individuals and executives. For instance, some hackers have attempted to capitalize on this security incident, with one reportedly offering to sell personal information on a public forum for striking $7000 worth of Bitcoin.
Adobe
Date: October 2013
Target: 38 million card records
In 2013, sensitive information from approximately 38 million individual users have surfaced on the dark web. This is still considered one of the most severe cyberattacks of the 21st century
The attackers successfully accessed:
- Account IDs and passwords
- Full names
- Credit/debit cards
- Specific product source codes
eBay
Date: March 2014
Target: 145 million exposed users
In 2012, the retailer has experienced a massive data breach, which exposed 145 million individual accounts. The hackers have gained entry into the network by acquiring login credentials from the company’s employees.
Financial information was luckily housed separately, which limited the impact only to:
- Full names
- Home addresses
- Email addresses
- Phone numbers
While, fortunately, no instances of following financial fraud were reported, it’s crucial to recognize that many reuse passwords across platforms, which increases the likelihood that some other services were compromised as well.
Equifax
Date: September 2017
Target: 148 million exposed users
In 2017, the credit reporting agency has faced a major data breach, which affected 148 million individual users. A custodian of highly sensitive information, the company has drawn heavy criticism for negligence and weak security measures.
The situation was tense:
- The breach originated from Apache Struts, an integrated third-party portal, and exploited a known security vulnerability in the backend code
- Despite patches for this security being available, the company has neglect ted to update its servers, which allowed the intruders to maintain data access for staggering 76 days
- What’s more, the company hasn’t renewed its certificates in a timely manner, which contributed to the delayed detection of abnormal data movements
- The company also granted their users broad permissions, granting access to more sensitive information than necessary
The company ultimately invested more than $1.4 billion to clean up the data damage and rebuild its defense.
River City Media
Date: March 2017
Target: 1.4 billion leaked records
From 2016 to 2017, the company has experienced one of the most extensive leakages in the entire history – the breach has resulted in exposed personal information of 1.4 billion individuals along with internal records. The majority of the compromised information comprised only email addresses, however, many also included full names, IP and physical addresses.
The company has shirked to enact password protection while arranging backup servers for its MySQL database. This oversight has persisted for over three months, during which over a billion individuals remained susceptible to exploitation by hackers.
Heartland Payment Systems
Date: May 2008
Target: 100 million card records
The company had suffered a serious data breach, which resulted in over 100 million card records being stolen. The inadequate security oversight has meant the company remained unaware of any illicit activity up until October 2008, five months after the data breach, when Visa and MasterCard have flagged strange transactions from their customer’s accounts.
The culprits were caught, the company, however, suffered irreparable damage – $200 million in compensation. Within months, their stock prices rapidly fell 77%.
Capital One
Date: July 2019
Target: 100 million personal records
In 2019, Paige Thompson, a former AWS employee, successfully hacked the company’s internal servers and got the access to trimming 100 million customer accounts along with payment information dating back to 2005. Compromised information included names, home addresses, bank accounts, and social security numbers.
The hacker has exploited an existing cloud firewall configuration vulnerability to execute multiple commands. She obtained administrator credentials to bypass the firewall to access data buckets and folders and copied and exported the information, which was then posted to GitHub.
Capital One has ended up settling a lawsuit in 2021 for about $190 million.
Cash App
Date: April 2022
Target: 8.2 million personal records
In 2022, the information from over 8 million individual users was downloaded by disgruntled former employee. The details included names, stock trading portfolios, stock trading activity, and brokerage account numbers.
And although no other personal information was stolen, the company has failed to implement access policies. What’s more, the attack has continued to happen over a 4-month period.
Cash App is currently undergoing multiple class-action lawsuits for failing to implement appropriate measures to protect their customers.
How we can help
Abto Software, with expertise in secure software development, assists partners in ensuring data protection. Our engineers, by prioritizing using security best practices, both deliver custom solutions and modernize existing applications to help our clients navigate today’s market conditions.
Insider threats, phishing attacks and ransomware, data breaches, credential stuffing, zero-day vulnerabilities – adopt efficient security mechanisms to focus on your business objectives and thrive.
Our expertise:
- Threat intelligence analysis
- Secure architecture design
- Data encryption
- Data protection
- Access controls
- Authentication mechanisms
- Vulnerability assessment
- Penetration testing
- Incident response
- Breach mitigation
Contact us and get a free project quote on your prospective project.


